| Codeforces Round 394 (Div. 2) |
|---|
| Finished |
After overcoming the stairs Dasha came to classes. She needed to write a password to begin her classes. The password is a string of length n which satisfies the following requirements:
- There is at least one digit in the string,
- There is at least one lowercase (small) letter of the Latin alphabet in the string,
- There is at least one of three listed symbols in the string: '#', '*', '&'.

Considering that these are programming classes it is not easy to write the password.
For each character of the password we have a fixed string of length m, on each of these n strings there is a pointer on some character. The i-th character displayed on the screen is the pointed character in the i-th string. Initially, all pointers are on characters with indexes 1 in the corresponding strings (all positions are numbered starting from one).
During one operation Dasha can move a pointer in one string one character to the left or to the right. Strings are cyclic, it means that when we move the pointer which is on the character with index 1 to the left, it moves to the character with the index m, and when we move it to the right from the position m it moves to the position 1.
You need to determine the minimum number of operations necessary to make the string displayed on the screen a valid password.
The first line contains two integers n, m (3 ≤ n ≤ 50, 1 ≤ m ≤ 50) — the length of the password and the length of strings which are assigned to password symbols.
Each of the next n lines contains the string which is assigned to the i-th symbol of the password string. Its length is m, it consists of digits, lowercase English letters, and characters '#', '*' or '&'.
You have such input data that you can always get a valid password.
Print one integer — the minimum number of operations which is necessary to make the string, which is displayed on the screen, a valid password.
3 4
1**2
a3*0
c4**
1
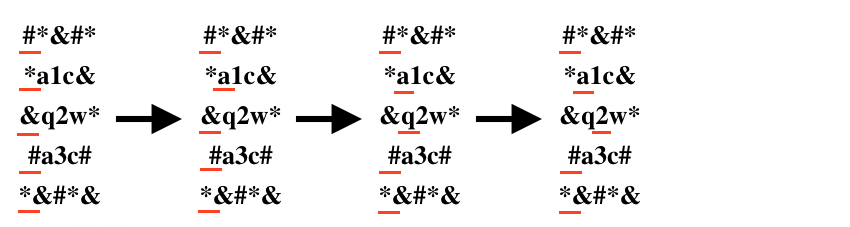
5 5
#*&#*
*a1c&
&q2w*
#a3c#
*&#*&
3
In the first test it is necessary to move the pointer of the third string to one left to get the optimal answer.

In the second test one of possible algorithms will be:
- to move the pointer of the second symbol once to the right.
- to move the pointer of the third symbol twice to the right.
| Name |
|---|




