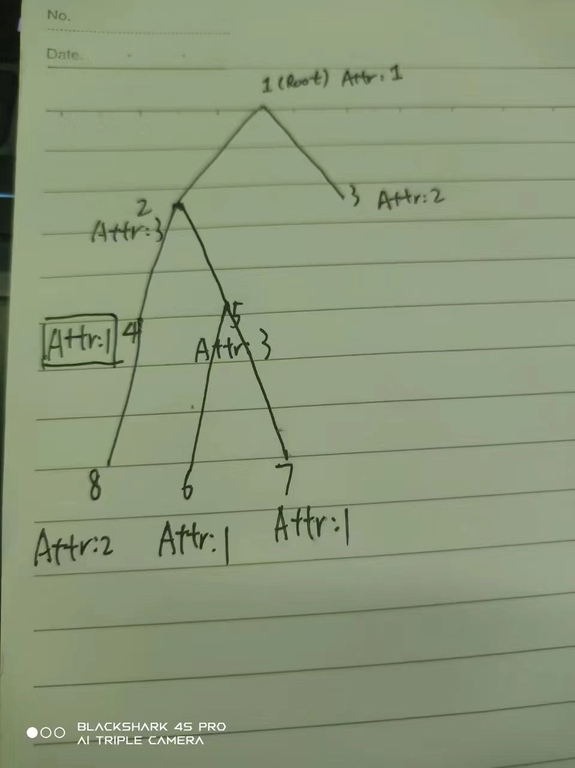
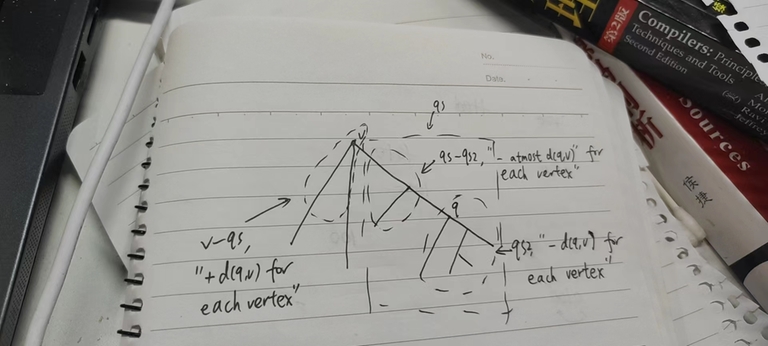
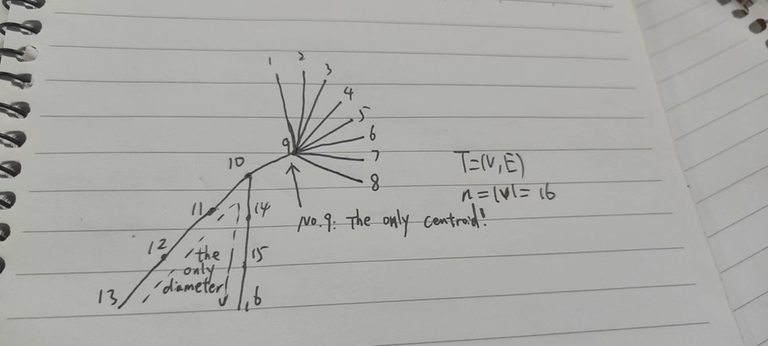
You just deleted my grandson dfsof's blog and banned him for 48 hours. Is CF a dictator? I hate dictators. Which rule did he violate, did you just ban him because he "offended" some admins?
Some top coders want to close dfsof's blog on MathStackExchange. Fortunately, MSE is democratic, after voting, the blog is still alive and gets some upvotes. Well, it is his first blog on PE, I never expected so many unpleasant issues to happen.
If CF is a dictator, I respect you. If CF only values top coders, I think at least I should quit.